Embracing Zero Trust in 2024: Why Trust is No Longer Enough
Building a More Secure Future with Zero Trust
Have you ever wondered if your current cybersecurity measures are truly sufficient in protecting your business from the sophisticated threats of today? As cyberattacks become more advanced, the traditional perimeter-based security models are proving inadequate. This brings us to the revolutionary concept of Zero Trust. But what exactly is Zero Trust, and why is it gaining so much traction?
Understanding Zero Trust
Zero Trust is a cybersecurity model that operates on the principle of “never trust, always verify.” Unlike traditional security models that assume everything inside the network is safe, Zero Trust continuously monitors and verifies every access request, whether it originates inside or outside the network. This model ensures that no one is trusted by default, making it a robust approach to modern cybersecurity.
Core Principles of Zero Trust
Verify Explicitly
Every access request must be authenticated and authorized based on all available data points, including user identity, location, device health, and more. This meticulous verification process reduces the risk of unauthorized access. Learn more about explicit verification from NIST Zero Trust Architecture.
Use Least Privilege Access
Users are granted the minimum level of access required to perform their tasks. This principle limits the potential damage in case of a breach. Detailed information can be found at CISA Zero Trust Maturity Model.
Assume Breach
Zero Trust assumes that a breach has either already occurred or will occur, prompting continuous monitoring and response strategies. This proactive approach enhances security resilience. Explore more about breach assumptions at CISA Zero Trust.
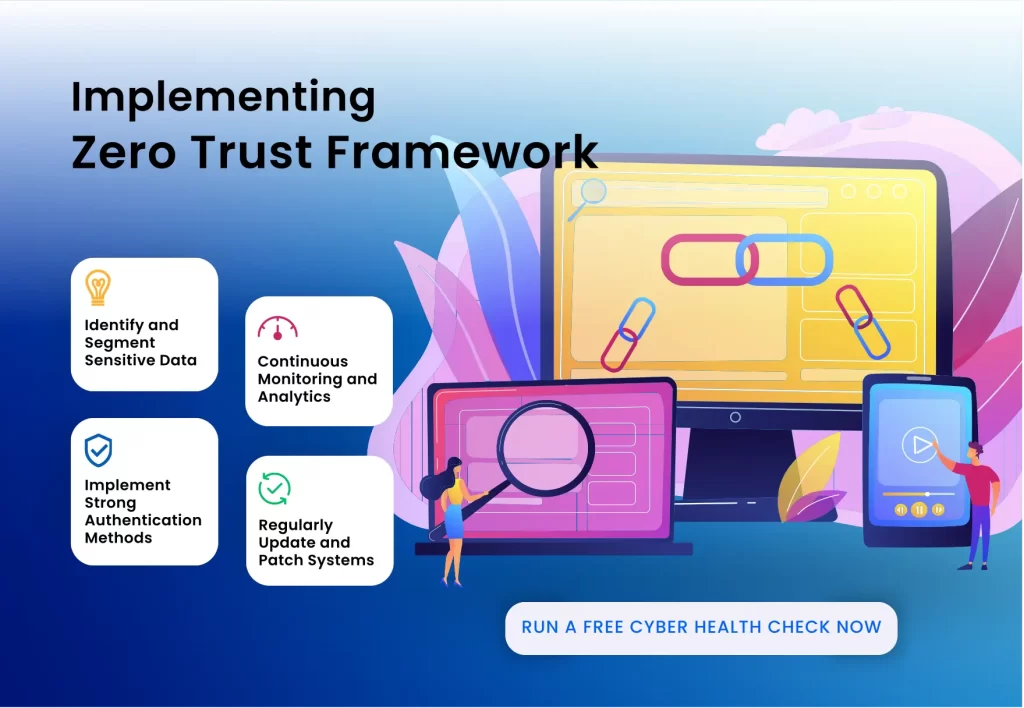
Implementing Zero Trust in Your Organization
Adopting a Zero Trust model involves several steps:
- Identify and Segment Sensitive Data Start by identifying your most sensitive data and segmenting your network to contain potential breaches. This minimizes the spread of malicious activity.
- Continuous Monitoring and Analytics Employ continuous monitoring and real-time analytics to detect and respond to suspicious activities promptly. This ensures threats are neutralized before causing significant harm.
- Implement Strong Authentication Methods Utilize multi-factor authentication (MFA) to add an extra layer of security. This ensures that only verified users can access your systems.
- Regularly Update and Patch Systems Keeping your systems and applications updated with the latest patches closes security gaps that attackers might exploit.
DataGuard365: Your Partner in Zero Trust Implementation
At DataGuard365, we specialize in helping businesses transition to a Zero Trust Framework. Our comprehensive services include network segmentation, continuous monitoring, and robust authentication solutions.

How Can DataGuard Help?
Special Offer: Free Cyber Health Check
To support your cybersecurity journey, we are offering a free Cyber Health Check for new clients. Contact us today to evaluate your current security posture and receive tailored recommendations to strengthen your defenses.
As cyber threats continue to evolve, embracing a Zero Trust model is no longer optional—it’s essential. By implementing Zero Trust principles, businesses can significantly enhance their security posture and protect their most valuable assets. Trust DataGuard365 to guide you through this transformative process.
Stay ahead of the curve with Zero Trust and DataGuard365.
Back to Articles/Blog